![Weaponized Hardware – Warning keep an eye out for any of these 4 suspicious devices on or around your network.]()
by John Costa | Nov 30, 2019 | Business Continuity / Disaster Prevention, Privacy, Safety, Security, Protection, Tech News
There has been a recent rise in the discovery “weaponized” hardware appearing on business networks world wide. “Weaponized” what? Hardware? Weaponized Hardware refers to physical devices which can be plugged into or attached to a network for the purpose of sniffing data or deploying injection attacks such as key-logging or ransomware deployment. Yes it is very dangerous.
Thanks to Black Hat security experts creating penetration tools to help IT security professionals detect and thwart cyber-attacks, it can comes as a backlash where nefarious attackers get their hand on the devices and use them for ill rather than for good. If you see anyone in or around your office with the infamous “pineapple” logo, you likely have a hacker in your mitz. The pineapple logo is the brand logo for HAK5, a company that creates and offers cyber-security emulation and detection devices to help network professional detect and block such weaponized hardware attacks.
A “Managed Firewall” can help detect and log activity from these “stealth” devices, which is why you should have a managed firewall on your network.
Weaponized Hardware
Here are a few of the most common “hiding in plain site” weaponized hardware attack devices:

This like a real mobile device cable. The O.MG contains a web server, 802.11 radio, and way more memory and processing power. The O.MG Cable is built for covert field-use by Red Teams, with features that enhance remote execution, stealth, forensics evasion, all while being able to quickly and dynamically change your tooling with minimal effort.
The O.MG Cable allows an attacker execute almost every feature via wireless, and not just creating, saving, or executing payloads. It can then be flash clean wiped to a convert innocuous state, which “break” the O.MG Cable so it will no longer pass data, and even flash new firmware therefore now making nearly impossible to detect that it was even deployed.
“Rubber Ducky” is the most famous where an ordinary looking USB flash drive is plugged into a computer or printer device on the network and begins deploying packet sniffing software which then reports back to the attacker via your network with the sensitive data the attacker is after, Nearly undetectable without the proper security polices and firewall setup “beforehand”.
“Signal Owl” is Screen Capture Device that can be attached to the back of a display device and record all the keystrokes and take screen snapshots behind the scenes unenclosed to the user or even the business owner.
Signal Owls are often see these devices in banks and retail outlets were the IT Dept or business owner intent is to monitor employee computer usage.
The issue is weather that stream is encrypted, if not it is vulnerable to “skimming” and the device itself can be hacked by someone else.
There are better ways to keep employees focused and bad stuff off your network. Like Firewall blocking of non-essential sites and an “Intranet” internal website to keep employees focused on work and not social media, news or shopping. The attackers simple physical presence in the environment can deploy a “signal owl” with- No access to your network!
“Shark Jack” plugs directly into any network “jack or network cable to deploy and do it’s dirty work.
There are even “weaponized mice” that can be purchased that are actually “spy” devices. (a good reason to buy from a reputable computer manufacturer rather than an off brand or used device.
This is a good reason to utilize a Managed, Monitored and maintained network via a reputable Cloud and Manged Services Provider such as South Bay Computer Solutions offering options to help keep your network safe from such devices and attacks.
These are just a handful of devices available on the market to would be – could be hackers.
If you see these logos on a backpack , sticker or the like, you likely have a “HAKer” in your mist.

This article is to keep you aware of what might be lurking in or around your network and how to spot them. Keep an eye out for expanded articles on these “spy” devices and how you might thwart them.

by John Costa | Nov 30, 2019 | Business, networking, Residential
A Firewall provides protection at the perimeter of your network. Most firewalls installed by your ISP or a junior technician are “dumb” firewalls. They are simply configured with some local rules and then left to become outdated as soon as they are installed. Furthermore power outages and field maintenance from the ISP’s e.g. Charter Cable often “wipe” or “reset” the firewall with no warning to you leaving you unprotected. A “Managed Firewall” is regularly monitored, maintained and administered. Firewalls are not a point-and-click or set-it-and-forget-it technology. Like most edge devices these days, firewalls are typically installed “on-site” or configured in the “cloud” and managed via “Remote Support”. ”
Managed Firewalls” allow live definitions to be updated which help protect against constantly changing threats. Rules can be set in place to block certain websites and social network activity. Cloud Firewalls are virtual firewalls with all communications run through the cloud security provider,
Managed firewalls typically provide for VLAN configurations which are Virtual Local Area Network keeping the VLAN seperate from the rest of the network
Make Managed Firewall your first line of defense.
Firewalls are a key component in safeguarding your business from malicious threats. Managed firewalls protect not only your “edge” devices, but your “cloud” perimeter “SaaS” and “Storage” areas.
Cloud based firewalls need no onsite hardware and help protect internet connected devices anywhere on the internet.
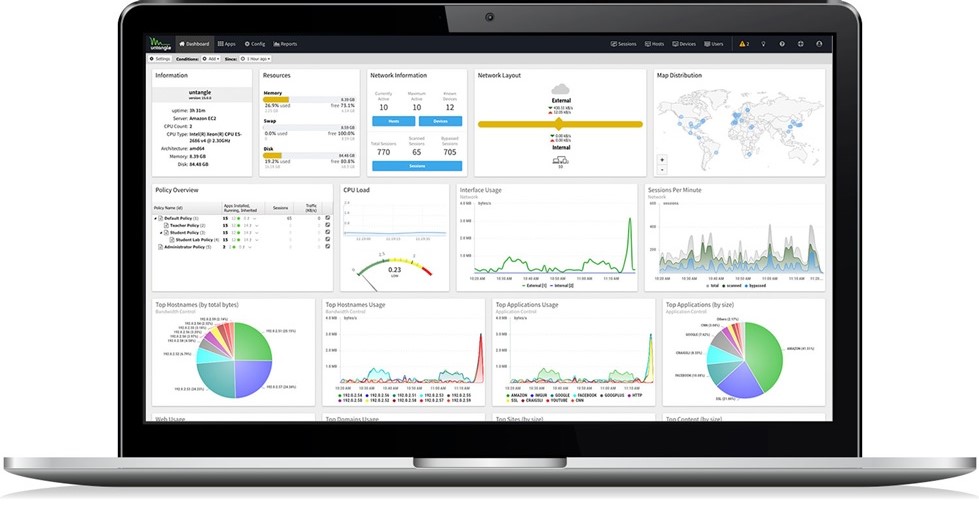
by John Costa | Nov 30, 2019 | Residential, Business, Cyber Security, networking
A Managed Firewall provides protection for devices at the perimeter (local in your home or office) and/or even on your cloud network. These devices are also commonly referred to as endpoints. Most firewalls installed by your ISP or a junior technician are static or “dumb” firewalls. They provide no real time monitoring or updating as needed to anticipate the latest “in the wild” threats. They are simply configured with some local rules and then left to become outdated as soon as they are installed. Furthermore power outages and field maintenance from your cable company or internet provider often “wipe” or “reset” the firewall with no warning to you leaving you unprotected.
A “Managed Firewall” is regularly monitored, patched and maintained. Firewalls are not a point-and-click or set-it-and-forget-it technology. Like most edge devices these days, firewalls are typically installed “on-site” , however the latest trend is to use configured in the “cloud” and managed via “Remote Support” managed Firewalls.
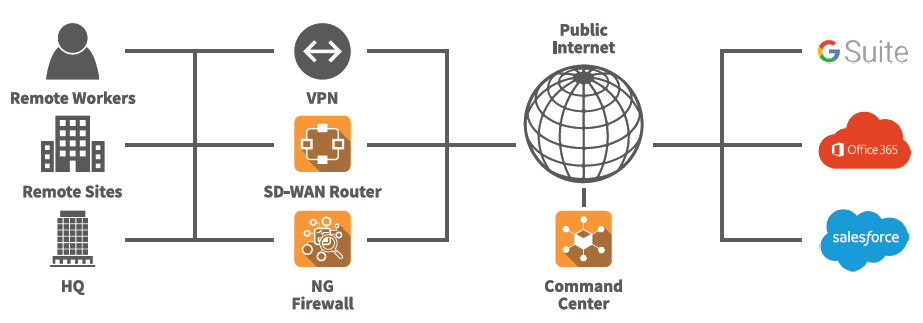
Managed Firewall Schema
Managed Firewalls” allow live security definitions to be updated which help protect against constantly changing threats. Rules can be set in place to block certain websites and social network activity. Cloud Firewalls are virtual firewalls with all communications run through the cloud security provider.
Managed firewalls typically provide for VLAN (Virtual Local Area Network) configurations which keep segments of the LAN separate from the rest of the network. For example security cameras and iOT devices are more easily hacked and there is no need for most employees to have access or even know these devices exist. So they are segregated into their own VLAN. VLAN’s can also be used to segment departments / business units like accounting, engineering, staff etc, as separate networks altogether.
Make a Virtual Managed Firewall your first line of defense.
SBCS recommends supports several perimeter and cloud manged firewall systems including Cisco umbrella, SonicWall, Untangle, Uplevel, O365 (yes, O365 has Cloud firewall capability.)
Protect your Office, Cloud and Remote Workers with a Virtual Firewall like the low Cost High Functioning Untangle. – See Untangle Fire Wall Data Sheet.
Drawing the line that separates internal and external networks, Firewall filters traffic based on IP address, protocol and port, which enables administrators to designate which systems and services (HTTP, FTP, etc.) are publicly available.
Firewall can be run as a transparent bridge to complement a pre-existing firewall and allows you to control inbound and/or outbound access to specific IPs and ports.
Firewalls are a key component in safeguarding your business from malicious threats. Managed firewalls protect not only your “edge” devices, but your “cloud” perimeter “SaaS” and “Storage” areas.
Contact Us if you would like help getting a Managed Fire Wall to protect your network.
by John Costa | Mar 31, 2019 | Tech News, Uncategorized
World Backup Day!
Is your data backed up? Can you restore your systems and files quickly in the event of a computer crash?
World Backup Day is the perfect day to check your backup status, for your home and your business.
You should be following the “1-2-3 Rule” at minimum, while reviewing and testing backups regularly.
1 = The “Working Copy” on your local computer / device.
2= “Local Copy” to a hard drive or network device on a USB Device or your network.
3= “Offsite / Remote / Cloud” copy on a secure storage server in the cloud.
If you’re are using offsite cloud services like IDrive, Carbonite or Acronis check your status and/or logs to make sure your important files are backed up and can be restored. It is recommended to regularly restore at least one file to a temporary folder then test open the file to assure it is indeed recoverable and readable.
Do you have a website? Be sure that is properly backed up on a regular basis as well. Believe it or not “most” web hosting companies “DO NOT” do a good job of backing up your website and databases.
CMS sites like WordPress and Joomla can be particularly finicky in the event of needing a restore is required.
Be sure you are using a quality backup service like Jetpack, Updraft Plus or WP-Clone. Ideally backup copies should be on a different storage location other than the server the website is hosted.
If your running an e-commerce shop on Shopify, Etsy, e-bay, etc. be sure you back that information up or have a copy of the content on your local drive, e-bay, in particular has been known to lose drafts and listings.
Using my secure remote support service is the best way to setup your backup, I have configured hundreds perhaps thousands of systems and can help assure your backups are configured and working. Get a full system Tune-Up / Security Check for extra peace of mind.
Just call 424-532-1633 or email to schedule a remote session today.
Download this FREE Microsoft Disaster Preparedness Business Plan eGuide and Disaster Preparedness Readiness Quiz to learn more.
Be on the look out for our Beyond Backup Solution.
Always On, Always Available, Anywhere, Any Device.

by John Costa | Feb 21, 2019 | Privacy, Safety, Security, Protection, Tech News, Tips & Tricks
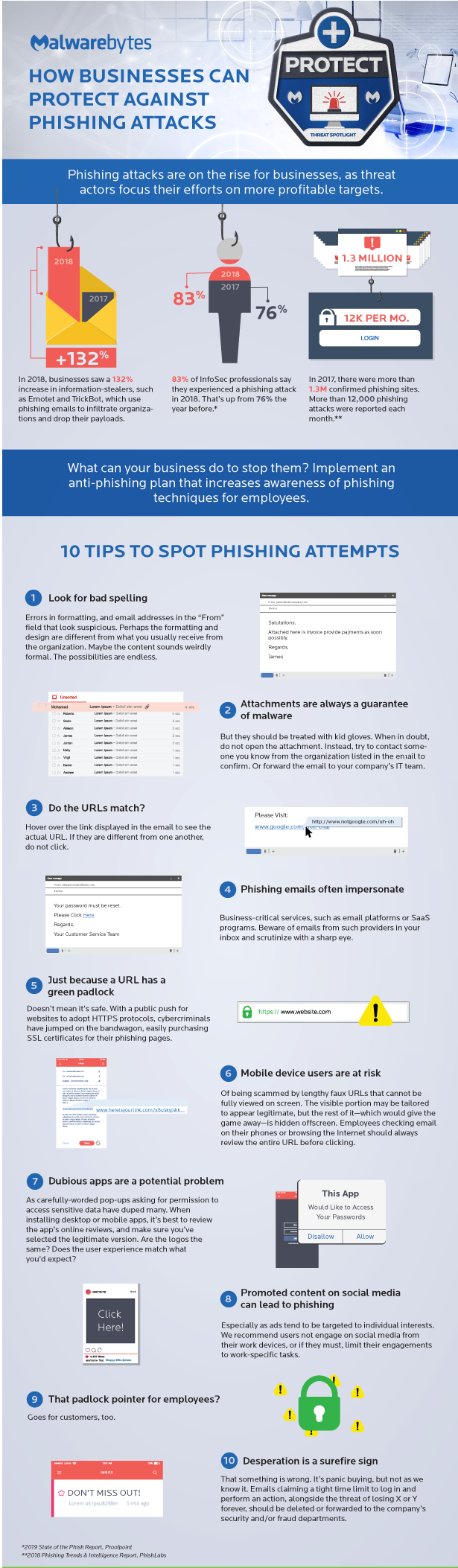
Phishing attacks are on the rise for businesses, as threat actors focus their efforts on more profitable targets. What can your business do to stop them? Implement an anti-phishing plan that increases awareness of phishing techniques for you and employees.
10 TIPS TO HELP SPOT PHISHING ATTEMPTS
In 2018, businesses saw a 132% increase in information-stealers, such as TrickBots which use phishing emails to infiltrate organizations and drop their payloads.
1) Look for poor spelling
Errors in formatting, and email addresses in the “From” field that look suspicious. Perhaps the formatting and design are different from what you usually receive from the organization. Maybe the content sounds strangely formal. The possibilities are endless.
2) Attachments are always a sign of malware
Attachments should be treated with kid gloves. When in doubt, do not open the attachment. Instead, try to contact someone you know from the organization listed in the email to confirm or delete the email without opening (RGHT-CLK – Delete) in Outlook.
Hover over the link displayed in the email to see the actual URL. If they are different from one another, do not click.
4) Phishing emails often impersonate
Attachments should be treated with kid gloves. When in doubt, do not open the attachment. Instead, try to contact someone you know from the organization listed in the email to confirm or delete the email without opening (RGHT-CLK – Delete) in Outlook.
5) Just because a URL has a green padlock
Doesn’t mean it’s safe. With a public push for websites to adopt HTTPS protocols, cybercriminals have jumped on the bandwagon, easily purchasing SSL certificates for their phishing pages.
6) Mobile device users are at risk
Of being scammed by lengthy faux URLs that cannot be fully viewed on screen. The visible portion may be tailored to appear legitimate, but the rest of it—which would give the game away—is hidden off-screen. Employees checking email on their phones or browsing the Internet should always review the entire URL before clicking.
7) Dubious apps are a potential problem
As carefully-worded pop-ups asking for permission to access sensitive data have duped many. When installing desktop or mobile apps, it’s best to review the app’s online reviews, and make sure you’ve selected the legitimate version. Are the logos the same? Does the user experience match what you’d expect?
8) Promoted social media content can lead to phishing
Especially as ads tend to be targeted to individual interests. We recommend users not engage on social media from their work devices, or if they must, limit their engagements
to work-specific tasks. Also, never go to social sites on critical systems like CAD/CAM workstations,Servers or mission critalce systems.
6) That Green Padlock in the URL bar ?
So, where does the green padlock come into play? The green padlock simply means that traffic to and from the website is encrypted. A certificate, provided by a certificate provider (Certificate Authority or CA), is used to set up this encryption. Sounds good, right? But the only thing you can actually be sure of when you see such a padlock is that your computer is connected to the site that you see in the address bar.
10) Desperation is a surefire sign
Kinda like dating, desperation is a sure sign something of trouble. It’s panic buying, but not as we know it. E-mails claiming a tight time limit to log in and perform an action, alongside the threat of losing X or Y forever, should be deleted or forwarded to he company’s security and/or fraud departments.
“Phishing is a method of tricking you into sharing passwords, credit card numbers, and othersensitive information by posing as a trusted institution in an email or phone call.
All about phishing
What is phishing?
Phishing is the crime of intending to deceive people into sharing sensitive information like passwords and credit card numbers. As with real fishing, there’s more than one way to reel in a victim, but one phishing tactic is the most common. Victims receive an email or a text message that imitates (or “spoofs”) a person or organization they trust, like a coworker, a bank, or a Government office. When the victim opens the email or text, they find a scary message meant to overcome their better judgement by filling them with fear. The message demands that the victim go to a website and take immediate action or risk some sort of consequence.
If users take the bait and click the link, they’re sent to an imitation of a legitimate website. From here, they’re asked to log in with their username and password credentials. If they are gullible enough to comply, the sign-on information goes to the attacker, who uses it to steal identities, pilfer bank accounts, and sell personal information on the black market.