by support@southbaysolutions.net | Nov 29, 2022 | Apps – Software, Business, Business Continuity / Disaster Prevention, Cloud, Privacy, Safety, Security, Protection, Residential
Our Top-Rated Best Computer Backup and Cloud File Access Cloud Tools for Home Users and Businesses Alike!
The best data backup software 2022. We began testing IDrive early on way back in 2002. Backup tools were really beginning to blossom, faster than we could keep up on reviewing, analyzing, testing, documenting, and publishing. Well today is no different, there are now literally hundreds of backup / restoration application programs available.
In this article, we’re going to review IDrive. We like IDrive for the price point and the array of advanced features it offers. It is relatively easy to Install, configure and mange. IDrive offers “In Cloud”, “Local On Premise/Your External Drive” and complete “System Image” configurations. One can back up several types of Data from PC / Mac systems to SQL databases, WordPress websites and any cloud storage provider data. E.g. Google Drive, Office365 and other cloud apps.
All of your backup data is under one web console. Very handy regardless of the number of devices, users, or data size.

Drive® e2 is a new add-on with fast, reliable, and affordable object storage solution with S3 API compatibility. It is an ideal solution for a second copy in the cloud, off-site disaster recovery, an active and accessible data archive, or long-term storage. While it is supports what most Amazon S3 API’s it does not support the following:
- Bucket/Object ACL (Alternatively, use bucket policies while creating an access key)
- Bucket specific CORS (By default, CORS is enabled in all the buckets)
- BucketAnalytics, BucketMetrics, BucketLogging
- BucketRequestPayment

As an Authorized Reseller we have been recommending, configuring, and managing IDrive online backup data protection for over 8 years now. We know firsthand how IDrive is rock solid backup and ransom-ware protection. A trustworthy online backup and sync solution for home users, nomad workers small businesses and enterprise workloads.
A recent Forrester report suggested that businesses are not protecting their computers and remote offices sufficiently. The lack of no backup or external drive scenario is prone to a lot of catastrophes such as loss due to theft or just plain data loss. Always use the 3to1 rule at a minimum for your data backup scenarios.
IDrive’s commitment to enhance user experience improves on a regular basis. Every feature of IDrive has been considered keeping in mind the view that IDrive backups should be simple and a ‘no-brainer’.
Backups, once scheduled, commence automatically and you can monitor the status of backups via an online dashboard, notifications on your devices or e-mail notifications. The backup and sync display full and accurate progress reporting. You are notified upon successful completion of operations.
Data Backup and Restore:
- PC’s
- Mac’s
- Servers
- Mobile Android and iOS
- Multiple Devices
- Websites
- WordPress via Updraft Plus Plugin.
- Most cloud applications data.
IDrive is ‘software as a service’ cloud data backup and offers complete system image backups.
IDrive is available as a downloadable desktop client utility. Backup PC’s, Mac, Servers, MS SQL, MS Exchange, VMware, Hyper-V, Microsoft 365, SharePoint, Oracle, and Linux.
I can tell you firsthand IDrive backup and most importantly restores files with excellent results. Many other backup offerings appear to backup, however restoring intact files can be a much different scenario. Always test restoring your data on a regular basis.
If you suffer a system crashes or ransomware attack, just go to your account on IDrive where your files are there for reading, downloading or restoring and IDrive is FAST! Plus you can get IDrive Express™ service to securely ship large amounts of data to the IDrive backup center or to you in the event of a disaster and needing a large data restore.
For further details on IDrive‘s compatibility with your operating platform for use within your organization, call us or visit IDrive with the link below for $90% off the 1st year! :
Need help? I can assist via a remote support session and telephone call. (424) 532-1633
Enterprise grade data backup for Servers, PC’s & VM’s at a fraction of the cost.

Multiple Device Backup
Backup multiple PCs, Macs, iPhones, iPads and Android devices into a single account.
In addition, data from external hard drives can also be backed up.
|
Cloud Drive
Files and folders will be synced in real time across all the devices that you link using Cloud Drive. The Cloud Drive storage does not impact your backup storage and matches your backup storage limit.
|
IDrive Express™
Quick backup and retrieval of data in less than a week via physical storage shipment, ensuring no bandwidth usage.
|
Snapshots and Versioning*
Snapshots provide historical view of data for point-in-time recovery and help protect against ransomware; IDrive retains up to 30 previous versions of all files backed up to your account
|
Manage Computers
Web-based console helps manage data backups, restores, application settings and more, on remote computers.
|
iPhone, iPad and Android Backup
Access files backed up from PCs and Macs or synced from connected devices; protect mobile data with apps for iOS and Android.
|
Clone/Computer Backup
Perform sector-level backup or file-level backup to secure your entire computer and restore the data to its initial state in the event of a disaster.
|
Powered by IDrive® e2Google Workspace Backup
Secure your entire Google Workspace data from accidental deletion or ransomware attacks with 3 automated backups per day and direct cloud recoveries.
|
Powered by IDrive® e2Microsoft Office 365 Backup
Enable automated backup for your Microsoft Office 365 users and quickly restore the backed up data in case of accidental deletions, cyber-attacks, and ransomware threats.
|
Security and Privacy
Transfer and store files with 256-bit AES encryption using a user-defined key that is not stored anywhere on the servers.
|
Continuous Data Protection
IDrive automatically recognizes the modified parts of files and backs them up.
|
Fast-Fast-Fast-Extremely Fast
Incremental and compressed backups will ease network bandwidth by transferring the modified portions of a file.
|
Retrieve Data
Search and restore files from the desktop application or via any browser; provision to recover deleted files from Trash within a period of 30 days.
|
Bare Metal Recovery
Perform image-based backup of your computers and local servers to new hardware with bare metal restore functionality. IDrive BMR enables you to backup the entire data stored in the hard disk; including the operating system (OS), application configurations and network drives.
IDrive BMR PRO – backup of your computers, local servers and virtual machines to a BMR
|
True Archiving
No data is deleted from the IDrive online account until you manually delete or run ‘Archive Cleanup’ to match your computer data to your account.
|
| |
|
|
Get Started with IDrive Online Backup and sign up for an IDrive account online.
Download, install and run IDrive Online Backup
Schedule backups of your data periodically or enable immediate backup.
Get the work done for you and make sure it is set up right with a South Bay Computer Solutions training overview session.
We offer 1 yr 5TB backup and remote installation, configuration and training starting at $189
Why Choose IDrive Online Data Backup?
- 5 GB for Free For Life – Larger accounts start at 2 TB cloud storage, plus 2TB sync space. You can back up an unlimited number of devices into one account.
- Military Grade Security – We use 256-bit AES encryption with an optional private key.
- Sub-accounts – Create unlimited sub-accounts within your storage space and monitor via a centralized administrator console.
- Server And Database Backup – Backup SQL, Exchange, Hyper-V, SharePoint, Oracle, Office 365 Mailbox, VMware, and Linux servers.
- IDrive® Thin Client – Deploy the IDrive® Thin Client application on your computers with minimal configuration and enable data backup via the web.
- Manage Computers – Manage data backups, restores, application settings, etc., on your distant computers via a web-based console.
- IDrive ExpressTM – Quickly backup and restore data via physical shipment of the Express device. The service is free 3X a year for business users.
- Single Sign-On – Configure your IDrive® Enterprise account for SSO with any IdP of your choice and enable hassle-free sign-ins.
- Business Compliance – Assistance to comply with regulations like HIPAA, SOX, GLBA, GDPR, and SEC/FINRA
Need help? We can assist via a remote support session and telephone call.
Email john@southbaysolutions.net or call (424) 532-1633 for assistance.

by support@southbaysolutions.net | Nov 28, 2016 | Privacy, Safety, Security, Protection, Tech News
“FBI now Recommends putting tape over your webcam / mobile camera”; I’ve recommended for sometime now, covering device webcam lens when not in use to help thwart unauthorized viewing.
Many are often in disbelief. They can’t really do that, can they? Or your just paranoid cause your a geek. “I don’t care if someone hacks my web cam.” It’s no longer a possible theory. Protect yourself. Pick up a LIGHT DIMS KIT – only $5.99 for 100 DIM stickers. Avoid the tacky look and gummy mess of roll tape. These little stickers do the job, easy removal and reusable. Share with your friends and family. Also, great for those never ending annoying flashing LEDs. Often those what were cool lights on electronic can become annoying, These help with that, quick, easy, non-permanent and inexpensive.
![Weaponized Hardware – Warning keep an eye out for any of these 4 suspicious devices on or around your network.]()
by John Costa | Nov 30, 2019 | Business Continuity / Disaster Prevention, Privacy, Safety, Security, Protection, Tech News
There has been a recent rise in the discovery “weaponized” hardware appearing on business networks world wide. “Weaponized” what? Hardware? Weaponized Hardware refers to physical devices which can be plugged into or attached to a network for the purpose of sniffing data or deploying injection attacks such as key-logging or ransomware deployment. Yes it is very dangerous.
Thanks to Black Hat security experts creating penetration tools to help IT security professionals detect and thwart cyber-attacks, it can comes as a backlash where nefarious attackers get their hand on the devices and use them for ill rather than for good. If you see anyone in or around your office with the infamous “pineapple” logo, you likely have a hacker in your mitz. The pineapple logo is the brand logo for HAK5, a company that creates and offers cyber-security emulation and detection devices to help network professional detect and block such weaponized hardware attacks.
A “Managed Firewall” can help detect and log activity from these “stealth” devices, which is why you should have a managed firewall on your network.
Weaponized Hardware
Here are a few of the most common “hiding in plain site” weaponized hardware attack devices:

This like a real mobile device cable. The O.MG contains a web server, 802.11 radio, and way more memory and processing power. The O.MG Cable is built for covert field-use by Red Teams, with features that enhance remote execution, stealth, forensics evasion, all while being able to quickly and dynamically change your tooling with minimal effort.
The O.MG Cable allows an attacker execute almost every feature via wireless, and not just creating, saving, or executing payloads. It can then be flash clean wiped to a convert innocuous state, which “break” the O.MG Cable so it will no longer pass data, and even flash new firmware therefore now making nearly impossible to detect that it was even deployed.
“Rubber Ducky” is the most famous where an ordinary looking USB flash drive is plugged into a computer or printer device on the network and begins deploying packet sniffing software which then reports back to the attacker via your network with the sensitive data the attacker is after, Nearly undetectable without the proper security polices and firewall setup “beforehand”.
“Signal Owl” is Screen Capture Device that can be attached to the back of a display device and record all the keystrokes and take screen snapshots behind the scenes unenclosed to the user or even the business owner.
Signal Owls are often see these devices in banks and retail outlets were the IT Dept or business owner intent is to monitor employee computer usage.
The issue is weather that stream is encrypted, if not it is vulnerable to “skimming” and the device itself can be hacked by someone else.
There are better ways to keep employees focused and bad stuff off your network. Like Firewall blocking of non-essential sites and an “Intranet” internal website to keep employees focused on work and not social media, news or shopping. The attackers simple physical presence in the environment can deploy a “signal owl” with- No access to your network!
“Shark Jack” plugs directly into any network “jack or network cable to deploy and do it’s dirty work.
There are even “weaponized mice” that can be purchased that are actually “spy” devices. (a good reason to buy from a reputable computer manufacturer rather than an off brand or used device.
This is a good reason to utilize a Managed, Monitored and maintained network via a reputable Cloud and Manged Services Provider such as South Bay Computer Solutions offering options to help keep your network safe from such devices and attacks.
These are just a handful of devices available on the market to would be – could be hackers.
If you see these logos on a backpack , sticker or the like, you likely have a “HAKer” in your mist.

This article is to keep you aware of what might be lurking in or around your network and how to spot them. Keep an eye out for expanded articles on these “spy” devices and how you might thwart them.
by support@southbaysolutions.net | Dec 1, 2019 | Privacy, Safety, Security, Protection, Tech News, Uncategorized
Well it is official.
Our past warnings and concerns over being monitored (spyed) upon through SmartTV’s is real. In addition to the now typical advertiser tracking, the provider themselves are tracking and serving content based upon your viewing habits. This is kept in a database just for you. Perhaps most importantly is the accessibility to microphones and cameras on smart devices, in particular Smart Tv’s. We have recommended covering laptop cameras and disconnecting desktop cameras when not in use.
These devices have now become known as “edge” devices as part of your “IoT” network, known as the “Internet of Things”. We affectionately refer to “IoT” as the “internet of Insecure Things.”
The FBI has now released a stark warning to users to cover smart TV cameras with tape as well.
We recommend having a managed secondary firewall to help monitor, maintain and protect your IoT network.
Welcome to the New World Order.
Keep an eye out for our recommendations on how to secure your “Iot”. Yes your refrigerator will be spying on you.

by John Costa | Feb 21, 2019 | Privacy, Safety, Security, Protection, Tech News, Tips & Tricks
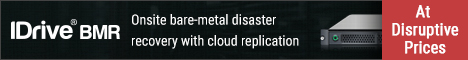
Phishing attacks are on the rise for businesses, as threat actors focus their efforts on more profitable targets. What can your business do to stop them? Implement an anti-phishing plan that increases awareness of phishing techniques for you and employees.
10 TIPS TO HELP SPOT PHISHING ATTEMPTS
In 2018, businesses saw a 132% increase in information-stealers, such as TrickBots which use phishing emails to infiltrate organizations and drop their payloads.
1) Look for poor spelling
Errors in formatting, and email addresses in the “From” field that look suspicious. Perhaps the formatting and design are different from what you usually receive from the organization. Maybe the content sounds strangely formal. The possibilities are endless.
2) Attachments are always a sign of malware
Attachments should be treated with kid gloves. When in doubt, do not open the attachment. Instead, try to contact someone you know from the organization listed in the email to confirm or delete the email without opening (RGHT-CLK – Delete) in Outlook.
Hover over the link displayed in the email to see the actual URL. If they are different from one another, do not click.
4) Phishing emails often impersonate
Attachments should be treated with kid gloves. When in doubt, do not open the attachment. Instead, try to contact someone you know from the organization listed in the email to confirm or delete the email without opening (RGHT-CLK – Delete) in Outlook.
5) Just because a URL has a green padlock
Doesn’t mean it’s safe. With a public push for websites to adopt HTTPS protocols, cybercriminals have jumped on the bandwagon, easily purchasing SSL certificates for their phishing pages.
6) Mobile device users are at risk
Of being scammed by lengthy faux URLs that cannot be fully viewed on screen. The visible portion may be tailored to appear legitimate, but the rest of it—which would give the game away—is hidden off-screen. Employees checking email on their phones or browsing the Internet should always review the entire URL before clicking.
7) Dubious apps are a potential problem
As carefully-worded pop-ups asking for permission to access sensitive data have duped many. When installing desktop or mobile apps, it’s best to review the app’s online reviews, and make sure you’ve selected the legitimate version. Are the logos the same? Does the user experience match what you’d expect?
8) Promoted social media content can lead to phishing
Especially as ads tend to be targeted to individual interests. We recommend users not engage on social media from their work devices, or if they must, limit their engagements
to work-specific tasks. Also, never go to social sites on critical systems like CAD/CAM workstations,Servers or mission critalce systems.
6) That Green Padlock in the URL bar ?
So, where does the green padlock come into play? The green padlock simply means that traffic to and from the website is encrypted. A certificate, provided by a certificate provider (Certificate Authority or CA), is used to set up this encryption. Sounds good, right? But the only thing you can actually be sure of when you see such a padlock is that your computer is connected to the site that you see in the address bar.
10) Desperation is a surefire sign
Kinda like dating, desperation is a sure sign something of trouble. It’s panic buying, but not as we know it. E-mails claiming a tight time limit to log in and perform an action, alongside the threat of losing X or Y forever, should be deleted or forwarded to he company’s security and/or fraud departments.
“Phishing is a method of tricking you into sharing passwords, credit card numbers, and othersensitive information by posing as a trusted institution in an email or phone call.
All about phishing
What is phishing?
Phishing is the crime of intending to deceive people into sharing sensitive information like passwords and credit card numbers. As with real fishing, there’s more than one way to reel in a victim, but one phishing tactic is the most common. Victims receive an email or a text message that imitates (or “spoofs”) a person or organization they trust, like a coworker, a bank, or a Government office. When the victim opens the email or text, they find a scary message meant to overcome their better judgement by filling them with fear. The message demands that the victim go to a website and take immediate action or risk some sort of consequence.
If users take the bait and click the link, they’re sent to an imitation of a legitimate website. From here, they’re asked to log in with their username and password credentials. If they are gullible enough to comply, the sign-on information goes to the attacker, who uses it to steal identities, pilfer bank accounts, and sell personal information on the black market.
by support@southbaysolutions.net | Mar 7, 2017 | Privacy, Safety, Security, Protection, Tech News
Cloud bleed was a Security Breech which involved leaked code for customers which use the CloudFlair platform. This include many BIG and SMALL companies for data storage, sharing, web hosting and websites. Cloud-flair has apparently fixed the issue. Essentially it allowed other “bad” sites to read information your browsers cache .
by support@southbaysolutions.net | Oct 18, 2017 | Tech News, Privacy, Safety, Security, Protection
A new vulnerability has been found in off the shelf routers including such as Netgear and Linksys. The bug is present in WPA2’s cryptographic code and can be utilized to trick a connected party into reinstalling a key which is already in use. While the code is meant to prevent replay attacks, in this case, attackers are then given the opportunity to replay, decrypt, or forge packets.
In general, Windows and newer versions of iOS are unaffected, but the bug can have a serious impact on Android 6.0 Marshmallow and newer.
The attack could also be troublesome for IoT devices, as vendors often fail to implement acceptable security standards or update systems in the supply chain, which has already led to millions of vulnerable and unpatched IoT devices being exposed for use by botnets and hackers.
The vulnerability does not mean the world of WPA2 is completely useless, but it is up to vendors to mitigate the issues this may cause.
The would be perpetrator would need to be within WI-FI range of your network to gain access. It is not something as of yet whcich can be accessed via the internet from half-way around the world.
RECOMMENDATION – Patch / Update your routers.
by support@southbaysolutions.net | Mar 8, 2016 | Privacy, Safety, Security, Protection, Tech News
A new strain of “talking” ransom-ware is beginning to appear.We’ve seen it on both Windows10 and Windows. In addition, apparently it being sold as service to hackers so practically anyone can use it. No coding experience is required. Ransom-ware is software which is dropped on a computer and runs through the network encrypting data files, rendering them un-openable without a “key” which the hackers attempt to sell to the victim so they can once again access their files.
The software verbally startles the victim and instructs them to pay the ransom.
NEVER pay a ransom, as there is no guarantee that they may easily become re-encrypted at a later date. In addition, there are remnants spread around the network which could reinfect.
Infected networks must be cleaned and secured. The best way to turn a would be catastrophe into a mere inconvenience is with “proper systems backup and disaster preparation“.
While there are plenty of “backup” tools available. We always recommend the “3-1” rule. (3) three copies of up to date data, with one (1) copy off-site.
by support@southbaysolutions.net | Mar 7, 2017 | Privacy, Safety, Security, Protection, Tech News
This Digitalprivacyalert.org redirect is caused by adware installed on your computer. Such adware programs are bundled with other free software that you download off of the Internet. It also appears when visiting infected websites. Unfortunately, some free downloads do not adequately disclose that other software will also be installed and you may find that you have installed adware without your knowledge.
Once this malicious program is installed, whenever you will browse the Internet, an ad from Digitalprivacyalert.org will randomly pop-up.
These ads are aimed to promote the installation of additional questionable content including web browser toolbars, optimization utilities and other products, all so the adware publisher can generate pay-per-click revenue.
When infected with this adware program, other common symptoms include:
- Advertising banners are injected with the web pages that you are visiting.
- Random web page text is turned into hyperlinks.
- Browser popups appear which recommend fake updates or other software.
- Other unwanted adware programs might get installed without the user’s knowledge.
RECOMMENDATION DO NOT FOLLOW THE PROMPTS OR INSTALL THIS PROGRAM. RATHER CLICK the “X” in UPPER RIGHT CORNER. THEN RUN YOUR Anti-Virus / Anti-Malware Program.
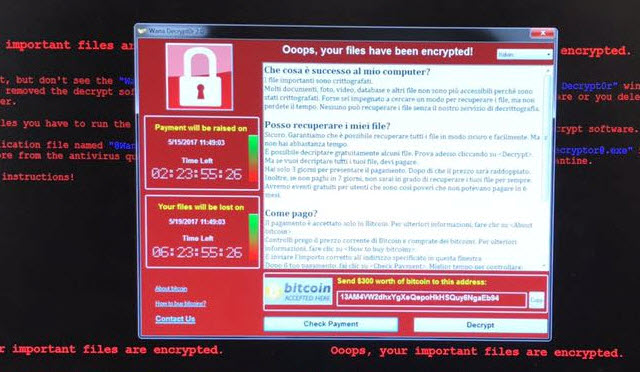
by support@southbaysolutions.net | May 15, 2017 | Privacy, Safety, Security, Protection, Tech News
WannaCry Ransomware Global Attack is current attack on company data across the globe. Europe was hard hit last week and it is expected the US will suffer similar attacks. Be extra careful opening attachments and links on other websites. In some cases legitimate websites are being targeted to spread the offending code. For example a hospital I recommend “Right-Clicking” and scan the file or link before opening.
The worst issue that is being dealt with by victims is this: the files touched by the attack are encrypted and the attacker is the only source for the key to reverse that. This can have dire consequences, especially in the healthcare sector. Encrypted patient records, doctor’s files and other items may not be usable or accessible unless there is a good backup to restore.
The code encrypts all files and changes the file extensions of files to .dharma. It then crawls the LAN and in some cases through VPN and Offline mounts.
Tips to try and avoid infection are :
- Keep operating system up-to-date and patched
- Use latest version of your Anti-Virus available
- Don’t open unwanted emails
- Right-Click and “scan” all attachments – even those whom are normally trusted resources as they may have been affected without knowing so.
- Dismount backup drives after backups complete as to isolate them from the Network.
- Remount prior to scheduled backup
- Have an Offsite Storage Plan like Carbonite or Code42
- One Drive and Dropbox files will be affected and therefore are not viable backups if mounted.
- Have a Virtual Machine Disaster Recovery System in Place such as StorageCraft ShadowProtect.
If you should fall victim to this attack, we can help. Better yet if you do not have a “Disaster Recovery Plan” in place call us today to help get your systems protected.
Do NOT Pay the Ransom, there is no guarantee the files will be de-encrypted or will not just suddenly re-encrypted again in the future.
The best defense is planning , preparation and active monitoring.